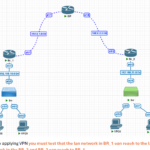
Final OSPF Configuration Lab
This is the final configuration lab, designed to check whether you have understood all the OSPF concepts we have seen in the course. If you successfully complete all configuration tasks,…
Top 5 Myanmar Software Tools You Should Download in 2025
In 2025, Myanmar users are more connected than ever. Whether you’re working online, typing in Burmese, or translating between Unicode and Zawgyi, having the right tools installed can make a…
Which two keywords can be used in an access control list to replace a wildcard mask or address and wildcard mask pair? (Choose two.)
Which two keywords can be used in an access control list to replace a wildcard mask or address and wildcard mask pair? (Choose two.) Explanation: The host keyword is used…
ACL Question
Refer to the exhibit. A router has an existing ACL that permits all traffic from the 172.16.0.0 network. The administrator attempts to add a new ACE to the ACL that…
The IT department is tasked to implement a system that controls what a user can and cannot do on the corporate network. Which process should be implemented to meet the requirement?
The IT department is tasked to implement a system that controls what a user can and cannot do on the corporate network. Which process should be implemented to meet the…
Which component of the zero trust security model focuses on secure access when an API, a microservice, or a container is accessing a database within an application?
Which component of the zero trust security model focuses on secure access when an API, a microservice, or a container is accessing a database within an application? Explanation: The workload…