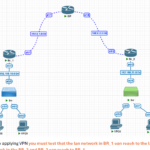
WPA2PSK Hacking Myanmar Version Download
ecuring a home network is not always easy – even if you take all the precautions you can. There are many factors that play into it and one is, of…
DeepSeek: The Chinese AI app that has the world talking
A Chinese-made artificial intelligence (AI) model called DeepSeek has shot to the top of Apple Store’s downloads, stunning investors and sinking some tech stocks. Its latest version was released on…
ကွယ်လွန်သွားတဲ့သခင်ကို စတိုးဆိုင်အရှေ့မှာ နေ့တိုင်းစောင့်နေခဲ့တဲ့ သစ္စာရှိခွေးလေး Moo Daeng
ထိုင်းနိုင်ငံ၊ကိုရတ်မြို့လယ်က 7-Eleven စတိုးဆိုင်ရှေ့မှာ ခွေးလေးတစ်ကောင်ဟာ ကွယ်လွန်သွားတဲ့ သခင်ဖြစ်သူပြန်အလာကို စောင့်မျှော်နေခဲ့ပါတယ်။ ထိုစောင့်ဆိုင်းနေတဲ့ပုံရိပ်လေးဟာ ဆိုရှယ်မီဒီယာအသုံးပြုသူများကို ၀မ်းနည်းတုန်လှုပ်စေခဲ့ပါတယ်။ Moo Daeng (ဝက်သားနီလို့ အဓိပ္ပာယ်ရတဲ့) ခွေးလေးကို အိမ်ခြေယာမဲ့အမျိုးသားတစ်ဦးက ပြုစုစောင့်ရှောက်ခဲ့တာဖြစ်ပါတယ်။ ထိုအမျိုးသားဟာ အသက်ရှင်ရပ်တည်ဖို့အတွက် အစားအစာနဲ့ ပိုက်ဆံကို အလှူခံတောင်းရမ်းပြီးတော့ Moo Daeng လေးကိုလည်း ၀၀လင်လင်ကျွေးမွေးခဲ့တာပဲဖြစ်ပါတယ်။ ညဘက်တွေမှာတော့ Moo Daengလေးနဲ့အတူ 7-Eleven…
KiKi Family
Hello everyone, let me introduce the second son of the Kiki family.🔷Name: Bahuvali 😬🔷 The second son among 9 siblings🔷Distinctive features: the ears are not trapped like other noses, but…
Max and Bella’s Big Adventure: A Tale of Friendship and Fun
Once upon a time in a small, cozy neighborhood, there lived a young boy named Ethan and his two best animal friends: Max, a playful golden retriever, and Bella, a…
The Powerful Bond Between Pets and Children
January 13, 2025 In many households around the world, pets and children share a unique and transformative bond. Whether it’s the loyal companionship of a dog, the playful antics of…
Taking Control of Your Finances: The Importance of Personal Budgeting
Intoday’s fast-paced world, it’s easy to lose track of our finances. Unplanned expenses, impulsive purchases, and a lack of financial awareness can quickly derail even the most well-intentioned budgets. However,…
Cryptocurrency Regulation
Cryptocurrencies have emerged as a transformative force in the financial world, challenging traditional systems and offering new possibilities. However, their decentralized nature and inherent volatility have raised concerns, prompting regulators…
Ongoing Wildfires Continue to Ravage the U.S. Amid Rising Concerns
As of January 2025, the United States is grappling with a series of devastating wildfires that have caused widespread destruction and loss of life, particularly in the western states. The…
The Rise of Artificial Intelligence: A Revolution in the Making
In the fast-evolving world of technology, few developments have captured as much attention and curiosity as artificial intelligence (AI). From self-driving cars to AI-generated art, the rapid advancements in this…